From September 2005 to June 2006 a team of thirteen scholars at the The University of Southern California's Annenberg Center for Communication explored how new and maturing networking technologies are transforming the way in which we interact with content, media sources, other individuals and groups, and the world that surrounds us.
This site documents the process and the results.
categories
infrastructure videos
Three scenarios for U.S. broadband access evolution originally produced for the Networked Publics conference by Walter Baer, François Bar, Shahram Ghandeharizadeh, Fernando Ordonez, Aram Sinnreich and Todd Richmond.
1. Neutralnet
It’s 2017. The U.S. government runs the national communication GRID (Government-Run Information Distributor), comprised of the country’s fiber optics, cables, and radio links. Access to the GRID is open to all, on an equal basis, for any application and any content. Most of the population now creates and shares media of all kinds—what their productions lack in polish and sophistication, they make up in imagination.
Thanks to the government-run GRID, there no longer is a divide between urban and rural areas. The open access GRID has ushered in the era of micro-politics: every conceivable constituency can propose any initiative at any time, and set up a virtual debate space, and e-voting mechanisms.
Neutral Net was set in motion in 1983, when the FCC forced the local phone companies to let all eEnhanced sService pProviders use their wires for free. Within a few years, thousands of Internet Service ProvidersISPs jumped at the chance to offer new services without the need to invest in costly networks. With the release of the Mosaic Internet browser in 1993, a new mass medium was born. Soon after, in 1995, DSL and cable modems turned the old phone and cable television networks into broadband always-on information networks.
During the next ten years, a multitude of innovators built upon the open Internet to offer new communication services that radically transformed people’s ability to create, share and access information.
In our scenario, in September 2010 the U.S. Congress decided it essential to preserve the Internet’s openness. Strict rules forbid all network owners, telephone, cellular, and cable alike, to discriminate among users. They are not allowed to favor any traffic, nor to charge different fees for different users or different applications.
Anybody can now provide any communication service over the carriers’ networks. Wal-Mart introduces low-cost “WAL-Media”: their branded combination of wired and wireless Internet access, voice and text communication, and film and video distribution.
In the next few years, amateur production of content explodes. YouTube and MySpace garner audiences that far surpass those of traditional television channels. Blogs have now replaced newspapers as most people’s primary source of news. The Net supports a vibrant public sphere in which all constituencies find a voice, a virtual town hall, and viral tools to mobilize voters and make their voices heard.
To sort through this massive amount of news, debates, games, music, video, and films, users rely on each other. Social filters, recommendation engines, and distributed online marketplaces allow them to find, discover, rank, and select materials that match their passions.
Every device on the network is a server, whether in homes, public places, small businesses, or civic organizations. They support peer-to-peerP2P communication tools;, distribute user-produced stories, songs, and videos; and, host collaborative spaces that bring together families, workgroups, clubs, churches, or citizens.
A growing number of cities build their own Wi-Fi and fiber networks to foster greater civic Internet use. However, funding for professionally-produced premium content starts to decline, partly because it is impossible to guarantee the network performance that would allow optimum delivery of that content and, partly because P2P distribution of pirated content proliferates (it is hard to maintain control over IP intellectual property now that a multitude of service providers operate over the networks).
By 2012, network owners are unable to raise funds to upgrade their networks. Verizon discontinues FiOS, and AT&T abandons project Lightspeed. Cellular networks never fully upgrade to 3G. The network owners decide to become pure bit -carriers, scale down their production and programming operations, and concentrate instead in on cutting their costs down to a minimum, retaining only skeleton maintenance crews.
Meanwhile, although content from millions of amateur sources is now available, Hollywood loses its pre-eminence as the world’s main center of content production. Instead, big-budget entertainment is now produced in countries like China, France, and India, where the network owners keep tight control over who distributes what, and can thus guarantee protection of their IPintellectual property.
By 2014, investment in the U.S. network infrastructure has now fallen so low that its derelict state resembles that of the nation’s bridges and roads. To ward off catastrophic failure, the U.S. government takes over all communication networks, consolidating them into the Government-Run Information Distributor (GRID). A new tax on advertising is created to fund the GRID.
By 2017, the GRID provides uniform Net access throughout the U.S. territory. The nation ranks a weak 29th twenty-ninth in the OECD’s assessment of broadband performance, but a dynamic community of users constantly invents new ways to squeeze extra bits out of the country’s infrastructure.
U.S. elites are dissatisfied with the poor performance of the national GRID. They live in tele-parks, the new gated communities, which tend to congregate in border -cities and ports, where they get easy access to foreign network head-ends and submarine high-capacity fiber.
2. TCNOtopia
In the year 2017, two huge TCNOs control broadband Internet access throughout the United States. Each TCNO has its own content affiliates who provide online entertainment, sports, games, and information to the consuming public. Their operational motto is “we create, you enjoy.”
The path to TCNOtopia began in 1969, when the first bits sped across a new computer network funded by the U.S. Department of Defense. Soon the elements of what would become the Internet were in place: an open architecture where users innovate at the edges of the network and E2E communications with no gatekeeper inside the network core, all of it riding on top of the nation’s phone network, providing little compensation to the telcos who had built that infrastructure. In fact, the Internet stands in sharp contrast to telephone and cable visions, which place intelligence, control, and innovation inside the network.
By 2007, the TCNOs provide more than 96% of residential broadband connections. But most of the real profits are made by firms who use the TCNO networks, such as Microsoft, Amazon.com, Google, Yahoo!, eBay, and Disney. Verizon and AT&T fight back with Internet television, offering hundreds of channels and thousands of hours of on-demand programs. Like the cable companies, they want to choose the content they deliver over their broadband pipes and not simply act as common carriers. AT&T’s CEO declares that Internet content providers will have to pay extra for fast broadband delivery.
In reaction, content providers join with consumer groups to persuade Congress to preserve network neutrality. But they get a chilly reception in Washington. Instead, Congress gives telcos authority to freely offer Internet programming and decide what traffic gets priority within their network.
2010: Based on the early success of Wi-Fi in Philadelphia and San Francisco, Google launches broadband wireless nationwide in partnership with local municipalities.
Verizon and AT&T, followed by the cable operators, offer contracts to Sony, Fox, Disney, and others for fast-lane Internet delivery of their online games, movies, video, and other content. Those who choose not to pay must accept standard delivery. This slow lane is where user experimentation is allowed, the only option for user-run servers, and P2P and other applications unaffiliated with the carriers. To enforce the separation, the TCNOs now scan all data packets. Customer contracts authorize carriers to screen for viruses, spam, copyright violations, and content of interest to government agencies. These contracts also limit the bits users can upload without paying substantially higher fees.
2011: Most large content providers are enthusiastic about fast-lane delivery. They can now charge higher fees for premium media experiences. But some, like Google and Microsoft, mount court challenges to packet scanning and prioritization as violations of users’ privacy rights and of network operators’ obligations to provide common carrier services.
2012: Flush with cash from content providers, TCNOs accelerate investment in fiber infrastructure and in-network innovations to achieve high performance. Dozens of new services, such as online multiplayer sports and games, become wildly popular. With full control over individual data streams, the carriers can craft compelling multimedia experiences for their customers. TCNO interface equipment in the home also optimizes the user experience, while preventing unauthorized copying of content or the bypassing of advertising messages.
Meanwhile, Google’s broadband wireless buildout has achieved initial success with four million subscribers in twenty-eight cities. However, security and reliability concerns arise after hacker attacks disable some fifteen thousand wireless-enabled computers in Chicago and Los Angeles. The TCNOs effectively use this security failure in their broadband marketing campaigns.
2014: The U.S. Supreme Court rules in favor of the TCNOs’ right to scan data packets and prioritize Internet traffic. The decision cites the need to ensure network reliability and protect customers from hacker-induced harm.
2016: The merger of Comcast and Time Warner creates a behemoth controlling 90 percent of the U.S. cable market and 60 percent of all broadband connections.
After reporting billion dollar losses, Googlezon (formed by the recent merger of Google and Amazon.com) abandons its municipal wireless partnerships. Some cities vow to keep their networks on the air, but it appears an uphill struggle against the dominance of TCNO broadband.
2017: Determining that only increased scale can compete effectively with Comcast Time Warner, the Justice Department approves the merger of AT&T and Verizon. The broadband duopoly has no serious rivals. It has brought affordable broadband to 85 percent of U.S. households, who love the network innovations that protect against spam and viruses, the e-sports leagues, and the high-definition entertainment they receive from TCNO content affiliates.
Political expression online is encouraged within the established political structure—primarily through the two dominant national parties that have negotiated fast-lane delivery for their candidates and issue messages. Other political organizations and civic groups must negotiate ad hoc arrangements, and few have the financial resources to assure fast lane delivery of their messages.
Still, some academics, artists, and other dissidents bemoan the loss of amateur content production and collaborative activity that flowed over the Internet in the early-twenty-first century. TCNO restrictions have virtually eliminated P2P communication among residential broadband users for content distribution, collaborative work, or social and political organization. Online distribution and collaboration are channeled through TCNO-controlled servers and routers. As a consequence, Internet content and applications now conform closely to established consumer tastes and traditional values. It is nearly impossible for an innovator that is unaffiliated with the TCNOs to gain a sizable Internet audience in the United States
But perhaps another eBay, Napster, Yahoo!, Amazon.com or Google is ready to emerge out of the competitive chaos in India or Brazil.
3. Automata
In the year 2015, the Internet addresses the last-mile challenge using a mesh network of wireless devices named AutoMatas. The traditional telcos are now relegated to routing the backbone traffic. AutoMatas are self-organizing devices that communicate with one another when in each other’s radio range. They may use access points available at hot spots for access to the telcos’ wired infrastructure. AutoMatas are now ubiquitous in society and a standard feature in all new vehicles. Their widespread use contributes to augmenting the capacity of the wireless mesh network that effectively transmits the last-mile traffic.
An early example of wireless ad-hoc networks is the use of short-range radios by truck drivers to communicate road conditions and socialize while traveling. The need to exchange information and communicate while in motion was later satisfied through the use of mobile phones, although this system does not operate on an ad-hoc mesh network. The origins of the wireless ad-hoc network organized around AutoMatas dates back to 1991, when Vic Hayes of NCR Corporation in the Netherlands invents Wi-Fi for use with cashier systems. Prior to his retirement in 2003, he shapes the design of standards such as IEEE 802.11a, b, and g, becoming the “father of Wi-Fi.” The devices that operate on this standard have a limited radio range in the order of tens of feet and offer bandwidths in the order of tens of megabits per seconds.
In the first years of the new millennium, a number of different events begin to lay the ground for the emergence of a wireless mesh network. Lightweight portable products with gigabytes of memory storage, such as the iPod, hit the market enabling the consumption of digital entertainment on the go. COVERGE 2001 is a first conference dedicated to convergence of automobiles and computers. Participants discuss standards for an in-vehicle multimedia network. Mesh networks emerge in neighborhoods using Wi-Fi devices based on IEEE 802.11a, b, and g and offering Internet services to their residents.
2009: Advent of Wi-Fi tailor-made for mobile vehicles. The technological leap to enable Wi-Fi on mobile vehicles occurs in 2009, when companies introduce products based on 802.11p, also referred to as Wireless Access for the Vehicular Environment (WAVE), offering radio ranges in the order of a thousand feet with bandwidths in the order of megabits per second. Such ranges make possible meaningful exchange of information between vehicles that are in motion and base stations.
2010: The U.S. Congress makes a significant part of the analog broadcast spectrum available for unlicensed use. Groundbreaking work in interference-avoidance techniques has enabled efficient use of this spectrum. This big-broadband wireless spectrum represents the future of wireless communications. The unlikely group of successful bidders for the spectrum is composed of EarthLink, Sony, Cingular, GM, and Toyota. While EarthLink and Sony are preparing for general distribution of wireless content, the car companies are observing this from the consumer’s end: soon vehicles will be capable of receiving massive quantities of wireless content reliably, and new vehicle designs in the works are incorporating these features.
2011: The year 2011 witnesses the development of AutoMata. These wireless devices, looking like iPods and weighing less than 10 ounces, store audio and video clips, implement navigation and GPS capabilities of an automobile, and detect one another for multi-player games that extend a physical world with virtual objects. AutoMatas include terabytes of storage, and several types of wireless cards such as cellular, 802.11g, 802.11p, and Bluetooth. These networking cards operate in a variety of radio ranges (from a few feet to miles) and bandwidths (tens of kilobits to hundreds of megabits per second). Numerous car manufacturers begin to combine the vehicle’s telematics, navigation, and entertainment systems into AutoMatas for new models. These devices plug into an in-vehicle network to guide a driver to a destination and deliver entertainment content. Its owner may carry the device and use it as a personal digital assistant and personal audio and video entertainment unit.
2012: Hackers publish the programming interface to AutoMata, adding features such as text-to-audio and a VoIP interface. Using a Bluetooth-enabled headset, a user may listen to e-mail messages. Consumer electronic vendors are quick to adopt these novel features, publishing official versions for download by all. This grassroots effort introduces many safety features for in-vehicle use. For example, when in radio range of one another, AutoMatas exchange traffic information and hazards such as icy road conditions. An elegant holder on the front dashboard of a car provides for both re-charging of the AutoMata and its view of the road in front of the automobile. A passenger may view what another vehicle’s AutoMata might be recording several minutes ahead. Insurance companies start to give incentives to drivers who use voice activated AutoMatas that warn them of road hazards.
2011: Competing AutoMata-like devices reach the market, driving down prices and improving their efficiency and capabilities. In addition an active community of programmers continue to develop applications and operating systems and standards for AutoMatas. Devices are everywhere, creating an ad-hoc mesh network that begins to produce and route growing amounts of Internet traffic. In particular, the planned pre-staging of popular content to make it accessible to the mesh network is effectively reducing the last-mile Internet traffic. Users begin to switch from home ISP subscriptions to maintaining their AutoMata connectivity, much like mobile phone usage affected standard telephone lines. Telcos point to the growing traffic created by the mesh network, and its lack of security, to insist on the need to manage traffic on the Internet backbone to justify the investment in increased capacity. There is a surge in spam and identity theft due to the increasing Internet traffic on the mesh network. Soon telcos develop enhanced certification methods for personal messages and improved cryptography techniques for security introduced by academics and other users of the network.
2014: GM and Ford introduce software for AutoMata, enabling cars from 2014 onward to drive without human assistance on certain freeway stretches. A valid driver’s license holder must sit in the driver’s seat and agree to the risks of using AutoMata. When an intelligent road stretch is encountered, AutoMata signals its driver that it may assume responsibility for driving the car. These devices communicate with one another to share information about icy road conditions, accidents such as chemical spills, and other emergency situations. Devices minimize accidents by slowing down and stopping when too close to one another.
There is a steady reduction in the use of mobile phones once the mesh network provides better coverage in most urban settings than the nonintegrated cellular networks due to the ubiquitous presence of the AutoMata. Mobile phone calls are now mostly conducted with the AutoMata using VoIP.
2015: An AutoMata is now the size of a company pin that one wears on a business suit. It records and stores hundreds of hours of phone and live conversation, along with hours of video recordings. Its battery works for days of usage. For their display, AutoMatas utilize TVs in a living room, a laptop’s display at work, a mobile phone’s display on the road, and a car’s navigation display or fold-down screen. New and inexpensive displays start to appear in automobiles and coffee houses. Menus at high-end restaurants turn into a display and a keyboard for AutoMatas.
A year after the introduction of automatic driving by AutoMatas, observing a significant reduction in the number of accidents, many insurance companies give incentives to those who employ AutoMata to drive. In collaboration with tens of insurance companies, the U.S. Department of Transportation deploys Internet wireless hubs on most highway stretches in the country. Its primary purpose is to increase road safety and enhance emergency response. This new infrastructure helps create an alternate Internet backbone to the mired telco network and its traffic-management practices. There is now an alternative backbone for delivery of delayed modes of communication, alleviating the load on the telco’s wired backbone infrastructure.
2017: In cities such as Los Angeles a growing number of people are driven by their AutoMata from place to place. A vehicle then has become an extension of both the office and home. Special content is released for in-vehicle entertainment systems, capitalizing on the enclosed nature of the vehicle to immerse passengers in an experience.
Bollywood of India finally supersedes Hollywood in revenues by generating content tailor-made for in-vehicle use. Widespread amateur production and improved social filters have enabled a broad dissemination of diverse content and ideas, effectively “fattening the long tail” for entertainment, commerce, and political movements. Every idea is capable of finding its audience, however, due to the large number of possibilities available, advertising on the Internet and on hardware is still able to shape public opinion. Much like important content producers such as Disney, powerful interest groups such as the NRA and Texans for a Democratic Majority promote their message through product placement on antivirus and antispam software and new equipment. In addition, content can be prioritized by pre-placing content through the access points to the mesh network for a fee.
Widespread use of AutoMata has lead to a decline of home ISPs; local Internet traffic is routed through the mesh network, and traditional telcos are relegated to routing part of the backbone traffic. Bandwidth and latency on the mesh network is affected by the number of AutoMata present.
New Media Survey at the Economist
Last week's Economist magazine carries a Survey of New Media.
The online version has interviews with David Sifry, Chris Anderson, Jerry Michalski, Paul Saffo and Andreas Kluth.
On Site at Networked Publics
This page aggregates information about how to join us blogging this conference, how to post and tag your pictures, blog entries, videos, and so on.
Power Mapping
Even as network culture displaces postmodernism, Jameson's aesthetic of cognitive mapping is flourishing. Critical spatial practice has gathered a huge collection of critical mapping projects and essays about mapping today. And if you haven't seen it, of course you should visit the essay that Marc Tuters (one of the coiners of the term 'locative media') and I wrote for the Networked Publics group, Beyond Locative Media.
Mobile manga beats out hard copy for lazy literati
Mobile manga beats out hard copy for lazy literati:
 Japan remains the world's undisputed manga monarch, but the way Japanese are enjoying cartoons is undergoing a fundamental change, according to Sunday Mainichi.
Japan remains the world's undisputed manga monarch, but the way Japanese are enjoying cartoons is undergoing a fundamental change, according to Sunday Mainichi.
"Though manga readership has been declining here for over a decade, Japanese comics are more popular overseas than ever before.
Among the main reasons given for the decline in domestic manga readership has been the proliferation of the Internet and mobile phones.
... NTT solmare has carved a tidy niche for itself after merging the competing interests and its "Comic Site" has become the biggest mobile phone site dedicated to manga in Japan.
"We've passed 10 million downloads since starting the service in August 2004," a spokesman for the Osaka-based mobile phone company tells Sunday Mainichi. "We get about 2 million to 3 million downloads a month."
via textually.org
Cyber-urban activism

My article entitled "Cyber-Urban Activism and Political Change in Indonesia" has just been published in Re:Activism issue of the Eastbound. Eastbound, a peer reviewed journal published in print and online, aims to create an international platform for Western and Eastern European researchers engaged in the multidisciplinary field of media and cultural studies. It features articles, reviews and interviews dealing with social and political implications of the rise of entertainment media and mediated popular culture, the appearance of global media players, and the spread of new forms of politics and information technologies.
The Re:Activism issue is actually a selection of papers followed up from Re:Activism conference held last year in Budapest.
My own article deals with the politics of space and spatiality of politics by looking at the interaction between cyberactivism and urban activism and how cyber-networks are extended to social networks in urban setting.
If you're interested to download my article or the whole issue, just go online. All articles are published under creative-commons license.
Networked Publics Conference and Media Festival April 28 + 29
Annenberg Center for CommunicationUniversity of Southern CaliforniaApril 28-29, 2006This two-day event is bringing together new media scholars and practitioners to exhibit and discuss the roles of audiences, activists, and producers in maturing networked media ecologies. The event is organized by the Networked Publics fellowship program (netpublics.annenberg.edu) at the University of Southern California’s Annenberg Center for Communication.
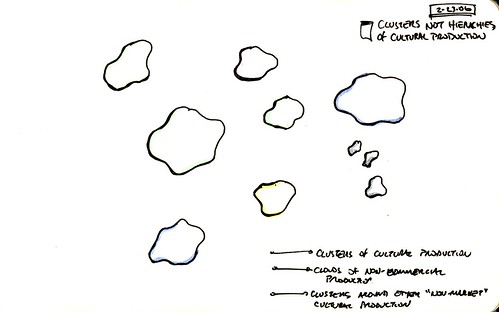
Clusters that Circulate Culture — Filling Out the Ecosystem Metaphors?
After the Yochai Benkler talk at the Annenberg Center for Communication I was thinking about different architectures, idioms and metaphors to describe the circulation of culture that was not hierarchical and not an architecture that predisposed one to ethically challenging responses, like..big business shapes culture and defiance doesn't work (resistance is futile, we'll all probably end up wearing Gap and we may as well get used to it..)
For what should be fairly obvious reasons, that sort of top-down architecture doesn't work very well for either explicating how culture circulates, or as importantly (these are the deep stakes) creating sustainable/habitable near-future imaginaries. That is, giving one (culture agents) a set of tools, resources, language, idioms, material instruments, means to make things, a decent HowTo guide and some FAQs - all of what one needs to imagine the world being otherwise and having the gumption and motivation to muster that world into existence. Although the bottom-up architecture/argument/explication is more empowering in that it gives a voice to individual culture agents/hustlers of culture, it does not adequately read or make legible the heavy duty power dynamics in the hierarchy.
Thinking about, now, clusters/clouds, not hierarchies, of cultural production/circulation. Clouds of non-commercial production, some commercial production, and vectors by which these clusters/clouds circulate meaning, drift apart, gather bits from encounters and bumps, through their own motility (sorry how that Googles..it'll change..) dissipate, lie in wait, evaporate and re-circulate in revived (retro'd) form.
Mimi, Yochai Benkler, Kazys and Adrienne and all the others at the dinner table deserve credit for discussing this.
Somewhere between the corporate tectonics and the bottom-up circulation/production of culture 2.0 is likely a more heterogenous geometry containing clouds that vector the dynamics of culture between and amongst all those (pretty much everyone who is a social being) who fab their social lives. Clusters of culture rather than hierarchies. Business practices are only one form of social practice, and no one practice can possibly determine another with such authority and certainty that either the bottom-up or the top-down hierarchical architecture holds up to strenuous argument.
Originally blogged at research/techkwondo
Technorati Tags: theory object
Annenberg Principles on Network Neutrality
The Annenberg Center for Communication, where I am a resident fellow this year recently brought together a group of senior communication experts from industry, academia, and consumer groups to discuss how to begin to bridge differences over the issue of network neutrality. Together, this group developed the Annenberg Principles for Network Neutrality, a set of key points to serve as a base for discussions on the topic in the future.
Annenberg Principles on Network Neutrality
The Annenberg Center for Communication, where I am a resident fellow this year recently brought together a group of senior communication experts from industry, academia, and consumer groups to discuss how to begin to bridge differences over the issue of network neutrality. Together, this group developed the Annenberg Principles for Network Neutrality, a set of key points to serve as a base for discussions on the topic in the future.
.
.